
Hackers sink to new low by stealing Discord accounts in ransomware attacks
AXLocker is a new ransomware attack that not only encrypts your files -- it also attempts to steal your Discord account, giving you 48 hours to respond.

Beware — even Mac open-source apps can contain malware
Your Mac isn't completely immune to hackers so watch out for this sneaky malware threat that pretends to be a helpful open-source app.
Half of Google Chrome extensions may be collecting your personal data
Data risk management company Incogni has found that half of every installed Google Chrome extension have a high to very high risk of collecting personal data.

Update Windows now — Microsoft just fixed several dangerous exploits
Microsoft has just fixed a whole lot of dangerous vulnerabilities as part of its latest Windows patch.

This Chrome extension lets hackers remotely seize your PC
Malicious extensions on Google Chrome are being used by hackers remotely in an effort to steal sensitive information.

This Wi-Fi security flaw could let drones track devices through walls
A research team from University of Waterloo has attached a device to a drone that can uses vulnerabilities in Wi-Fi networks to see through walls.

Hackers are infiltrating news websites to spread malware
The latest cybersecurity attack takes advantage of your trust in news sites and your browser to trick you into downloading malware.

This creepy Mac app can record every moment of your online life
A new app for your Mac claims it can record every moment of your online life and store it for retrieval.
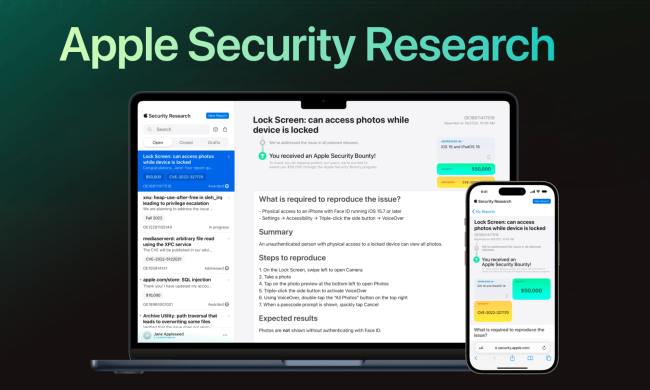
Apple Security Research website launches to protect your Mac
Apple is making it easier to research security flaws in macOS and iOS with its new website, which also serves as a reporting hub and information resource.

Here’s how much faster Nvidia’s RTX 4090 is at cracking passwords
You need to start using 2FA and a password manager since the latest research shows how much faster Nvidia’s RTX 4090 is at cracking passwords.

Typos can get you hacked in latest cybersecurity threat
Fake websites look just like the real ones, but steal your logins, harvest cryptocurrency, and infect your computer and phone in the latest cybersecurity threat.

Are Windows 11 security features killing your gaming performance? You might be surprised
Windows 11's security features kill your gaming performance, right? Microsoft brought this year-old issue back up, and we think it is high time to revisit it.

Passwords are hard and people are lazy, new report shows
Survey finds that online security is too difficult and most of us simply won't bother with multiple,strong and unique passwords.

Microsoft data breach exposed sensitive data of 65,000 companies
Microsoft is in a disagreement with a security research firm regarding how a recent breach of its servers has been handled.

DuckDuckGo’s new browser could help keep Mac users safe on the web
DuckDuckGo's privacy-first web browser has moved from the iPhone to the Mac and it might have even more security and safety than Apple's Safari.

The latest Firefox release redesigns its private browsing feature
Mozilla shows off its Private Browsing mode updates and design makeovers for Cybersecurity month.

Microsoft Edge now warns when your typos can lead to being phished
Microsoft has added a new feature to its Defender SmartScreen service to protect users from landing on typo webpages that might be phishing scams.

This new malware is targeting Facebook accounts – make sure yours is safe
Ducktail malware started as a threat to only Facebook Business accounts, but now everyone is in danger. Here's what you need to know to protect your account.

Microsoft just gave you a great way to fight Windows brute-force attacks
Windows is about to become more secure with a recent update from Microsoft that should block a large number of brute-force hacking attempts.

As ransomware hits this U.S. hospital, lives could be at risk
One of the nation’s largest hospital chains is suffering from a ransomware attack taking computer records offline for nine days, while patients wait.

New COVID-19 phishing emails may steal your business secrets
Google Forms are being used by cybercriminals as a way to obtain sensitive information of business owners through COVID-19 phishing emails.

Is there a NordVPN Prime Day deal?
If you're looking for a great online suite, the NordVPN Complete package is 64% off and comes with three free months. Grab it before October Prime Day is over!

This dangerous new hacker tool makes phishing worryingly easy
Setting up phishing campaigns for Microsoft 365 has become a relatively straightforward process due to a phishing-as-a-service (PhaaS) platform named Caffeine.

Intel Alder Lake BIOS source code was leaked — should you be worried?
Intel has confirmed that the source code for the Alder Lake BIOS was leaked. What will the consequences be?

Over 1M credit cards just leaked to criminals on the dark web
Over 1.2 million credit cards have been distributed via the dark web through a recently launched underground marketplace.

Meta found over 400 mobile apps ‘designed to steal’ Facebook logins
Meta has published a report detailing its discovery of over 400 mobile apps that were created to steal Facebook users' login information.

Google Chrome tops this list of most vulnerable browsers
Google Chrome suffered more vulnerabilities than any other browser in 2022 -- and it wasn't even close -- while a little-known browser had zero.

Hackers have found a way to hack you that you’d never expect
A security flaw has allowed a ransomware gang to effectively prevent antivirus programs from running properly on a system.

A new phishing scam pretends to be your boss sending you an email
A business email compromise campaign deceives a company employee into thinking their boss is authorizing a payment, but it's actually a bad actor.

New phishing method looks just like the real thing, but it steals your passwords
This new phishing method could make it possible for hackers to steal important data by cloning a trustworthy website or app in Application Mode.

This dangerous vulnerability tricks researchers by mimicking old threats
The CVE-2022-41040 and CVE-2022-41082 zero-day flaw has been brought to Microsoft's attention after its Exchange email servers were left exposed to bad actors.
How to create a new team in Microsoft Teams
Microsoft Teams allows you to organize your group based on different teams for different projects. Here's how to create and customize those Teams quickly!

North Korean hackers create fake job offers to steal important data
Microsoft has found that North Korea-based hackers have been using various software and creating fake jobs to carry out malicious cyberattacks.

This dangerous hacking tool is now on the loose, and the consequences could be huge
A dangerous hacking tool has just been cracked and is now spreading quickly, potentially putting countless people at risk.